User Agent Spoofing: What Is It & Why Does It Matter?
Jeffrey Edwards
|Cyber Risks & Threats | January 13, 2023

There are a number of practices used for hiding fraudulent practices online. One of these is User Agent Spoofing, also referred to as UA spoofing or browser spoofing.
Although user agent spoofing does have some legitimate applications, particularly for software developers, it is often used to carry out ad fraud and other forms of online deception.
So far, so technical… Why should you care about user agent spoofing, and how does it impact the average business owner or digital marketer?
To answer the question ‘What is UA spoofing?’, we need to first look at the basics.
What is the user agent string?
The user agent string, also referred to as the UA or UAS, is a code snippet presented by a web browser such as Chrome or Firefox to a website’s server.
Within the UA string is information about the web browser, the software version, and the device operating system – among other features.
The reason for presenting the user agent string is so that the site knows how to present the information (Is it a mobile site? Is it an old version of a certain browser?). So a website receives the information from the user agent string and, voila, here’s your website, sir. Enjoy the browsing experience.
Why is user agent spoofing useful?
For web developers, adjusting the UA string can help to check the compatibility of websites on different devices and browsers. In fact, many will employ a user agent spoofing Chrome extension or plugin to help them adjust their UAS on the fly – a popular method of testing websites or browser compatibility.
Some marketers may also use user agent spoofing to see how their ads, for example, display campaigns, are showing on different browsers. This can help them troubleshoot display issues or simply see how the images look on a browser that they wouldn’t otherwise have access to.
So, user agent spoofing isn’t always a malicious practice.
But, as you might already be able to see, it can easily be used by fraudulent parties. In fact, in theory, a spoofed UA string shouldn’t need to be used out in the wilds of the internet.
How can the UA string be used for fraud?
The most obvious way to use a spoofed user agent string for ad fraud is to present a hidden or custom browser as a genuine user.
But the clever part is that the browser sends a different custom user agent string each time it visits a website, therefore presenting itself as a unique visitor.
In short, you can click multiple times from one browser or device but make it appear that they are multiple unique visitors. You simply need to change the user agent string each time you click the link, which is done automatically if you use an extension on Mozilla, Chrome, or any custom browser.
This form of device obfuscation allows the fraudulent party to click on paid search results or to host display ads without being spotted by the ad platforms.
Device obfuscation
Bot farms and click farms tend to operate either from server centers or linked smartphones. And they’re often in the sort of locations that aren’t targeted by digital marketers – for example, Central Asia, China, or the Philippines. By changing the user agent, a bot farm operator can make their network of outdated Android smartphones look like clicks from a Mac in California.
Fake impressions
The method of invalid traffic blocking that Google and Facebook use can be fooled by inserting a custom user agent string. As such, a click farm or other source of fake traffic can change user agent strings to make it seem that they deliver genuine traffic.
Out of geo clicks
Browser spoofing using UA spoofing also allows fraudsters to change geographic settings such as device language, time zone, or other location-specific data. Again, this allows click farms or bot farms to offer ‘genuine’ traffic from a specific region or country. If you’ve ever wondered how you can buy ‘genuine organic USA clicks,’ then this is the answer. And no, they’re not genuine or organic.
Blocking fake traffic
Spotting and blocking bots has become a bit of a cause celebre, thanks in part to a certain Elon Musk’s comments on the matter.
In fact, the Twitter bot debate highlighted something that many in-the-know marketers already know: There are a lot of bots out there, and no one really knows how many.
The ad platforms, including Google and Facebook, are obviously aware of the problem. And yes, they do have measures in place to block fake traffic, including bots and click farms.
Facebook regularly runs an audit on users and clears out the suspected bot accounts. Google uses a number of methods to block fake traffic and refund advertisers who have had their ads clicked by bots or web scrapers.
But…
Is this enough?
Most marketers feel that it isn’t. With Google estimating an invalid traffic (IVT) rate of between 1-8%, which is the average rate in Google Analytics for many PPC marketers, the true figure has been shown to be much higher.
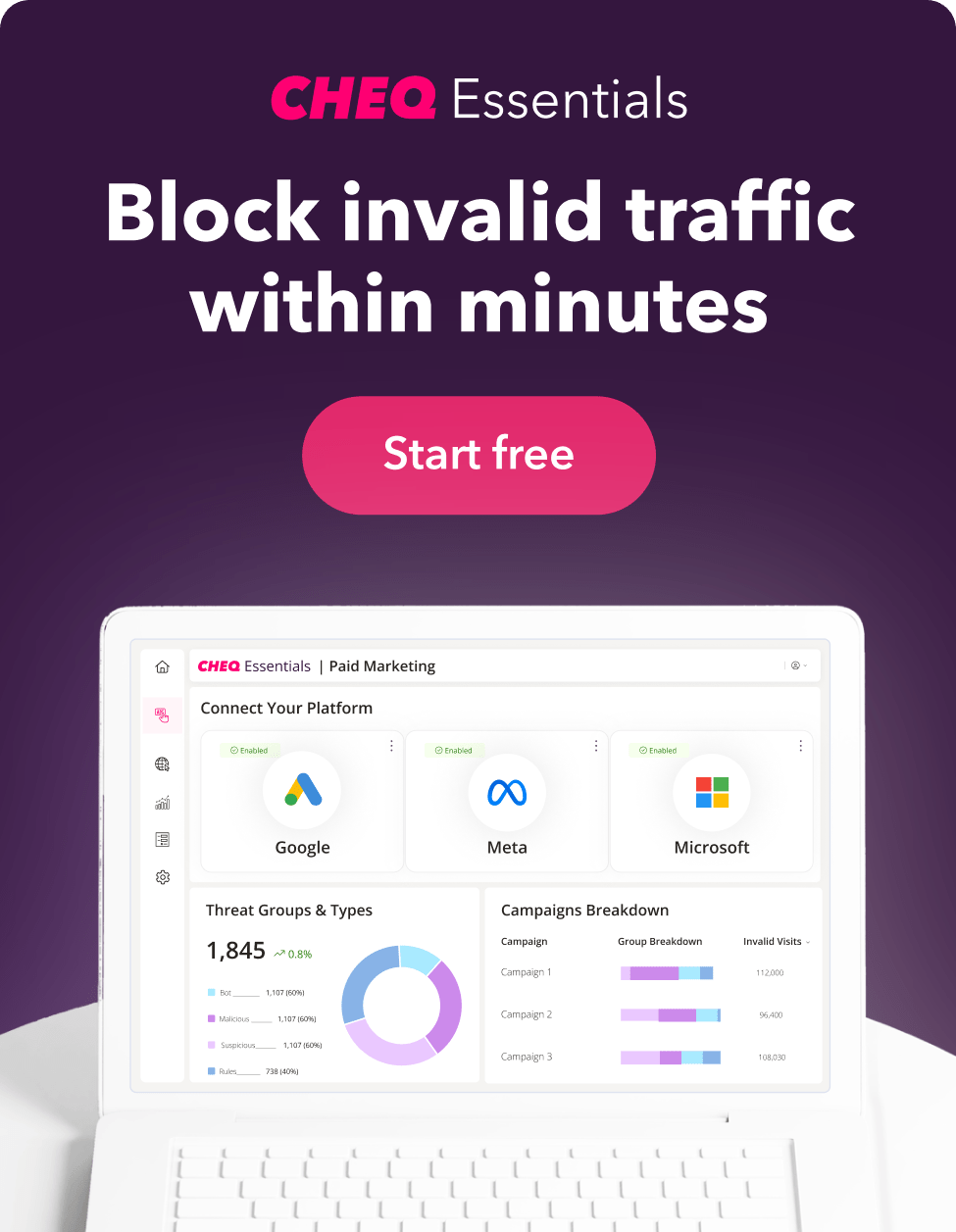
Here at CHEQ Essentials, we see an average of 14% of clicks on PPC campaigns that are non-genuine. This rises as high as 60% or more for some competitive industries.
Why is there such a big difference between us and Google or Facebook?
It’s all in the device fingerprinting.
CHEQ Essentials is a service dedicated to monitoring and blocking click fraud. Yes, CHEQ Essentials will identify mismatched devices, spoofed browsers, or other details that don’t match with their device.
If you’re running paid ads on Google, Bing, or Facebook, you can run a FREE traffic audit to see how much is picked up as IVT.