The Difference Between a Computer Virus, Worm, and Trojan Horse
Oli Lynch
|Cyber Risks & Threats | September 08, 2023

Any savvy internet user knows to watch out for computer viruses. But then, sometimes there’s a Trojan horse in your email. Or maybe a worm or bot has accessed your computer?
OK, hold up.
When it comes to making sense of the types of computer viruses out there and how they work, you don’t need to go too deep. But it is increasingly important to understand the digital threats out there and how to avoid them.
So we’ve put together this short guide to help you make sense of what is a trojan, a virus, a bot, and a worm.

Trojan Horse
You may remember the Greek myth of a wooden horse full of soldiers, which was used to sneak behind enemy lines so they could, basically, kill everyone.
The computer version of a Trojan Horse is a form of malicious software that remains dormant until a certain trigger action. That could be a set amount of time, an action on the host device, or a prompt from the command center.
Once it is in-situ, a Trojan can do all kinds of sneaky things. Luckily, they can’t kill you though…. Yet.
But they can:
- Steal data
- Delete files
- Perform proxy tasks such as cryptocurrency mining
- Be used for advertising click fraud
- Spreading other harmful files (see below)
- Exploiting vulnerabilities and letting malicious agents into the database
An example of a Trojan Horse used for click fraud is MIUREF, which has been around since at least 2013 and is still active today. In fact, MIUREF was used in one of the most infamous cases of organized click fraud, the 3ve and Methbot botnets.
You can read more about those in our post about these two ad fraud campaigns.
How to avoid Trojans
Like that big wooden horse of death, you can only get a Trojan on your system if you let it in. This usually involves action on the part of the user (you), which might include:
- Downloading and opening a file (could be something as innocuous as an email attachment)
- Running software from a suspicious source
- Using an attachment such as a USB stick containing malicious software
To avoid being infected by Trojan Horses on your computer system, avoid downloading or running any files on any of your devices if you’re not 100% sure of their source.
Be wary also of removable drives that aren’t yours or of using things like novelty USB devices. There are cases of computer viruses, including Trojan Horses being loaded into seemingly innocent removable drives.
Use a virus scanner on your device and run it regularly to find and remove Trojan Horses.
Virus
Like viruses in the real world, these sneaky bits of code are capable of spreading themselves, self replicating, and even mutating or evolving. This form of malware can go undetected by the user and can perform all manner of malicious actions.
The term virus and malware is often used interchangeably. But malware is any type of software that is compromised by all of the components on this list.
Much like Trojans, viruses find their way onto devices such as computers or cellphones through installs. This can be an app, a browser extension, an executable file as an attachment, or if you don’t wash your hands after coming back from the shops.
OK, maybe not that last one.
A particularly shady way for viruses to spread is in ‘viral content’ such as images, audio files, or videos. So, it’s possible to be infected by a computer virus if someone sends you an infected gif, video, or picture.
How do digital viruses spread?
Viruses can hijack software or find and exploit flaws in your computer, system, or network. Once they find a way to system, can be pre-programmed to carry out a task such as:
- Sending out files from infected software on your device (such as email clients)
- Scanning your computer to steal data/keystrokes, etc
- Carry out DDoS attacks as part of a network
An intriguing recent development is malware on the Google Play store, which is usually ‘side loaded’. This basically means that apps are clean when installed but that some additional code is added during an update or by exploiting a security vulnerability.
This code then acts as a virus and can carry out an activity such as displaying intrusive ads or performing a malicious activity in the background without the user’s knowledge.
Another method is malware injection, or SQL injection, which uses bots to add malicious code to a software package, such as an app or a website.
What is malware injection? Read more here.
How to avoid and protect against digital viruses
Like any malware or digital infection, protecting against computer viruses takes a little bit of savvy and, mostly, common sense.
- Avoid downloading software from suspicious sources
- Be wary of opening email attachments from non-trusted senders
- With Android apps, make sure to only use the Google Play store to install and, ideally, research your app first. If it has bad reviews for performance or intrusive ads, avoid it

Worms
A computer worm is a form of virus, specifically the type that self-replicates. These computer worms basically perform malicious actions in the same way that a virus or Trojan Horse would.
Worms will scan their local network or search the internet from their host device, looking for vulnerabilities to exploit. Because they are performing a process, e.g.; looking for more targets to infect, a computer worm can use up system resources, causing devices to run slower or even crash or become glitchy.
Although the worm may not perform a specific malicious activity, it can exploit security flaws to allow other viruses or bots to enter a computer network.
Like many other forms of malware on this list, worms can also use a ‘logic bomb.’ That sounds like something that intellectual terrorists would use, right? Actually, it’s a set of circumstances that, once met, can activate viruses or Trojan Horses.
For example, a worm might remain dormant until a certain set of keystrokes or a certain program is updated. Once the criteria are met, the virus will be activated and start carrying out its malicious duty.
How to protect against worms
Again, it’s a case of common sense and avoiding downloading anything suspicious. Attachments in emails, links in instant messages from unknown sources, pirated software, and websites that are crammed full of spammy pop-ups are all hotbeds of worm and virus activity.
Run a regular anti-virus scan on your device to weed out those pesky worms.
Bots
Short for ‘robots’, bots are pieces of code that are normally programmed to do a specific task. There are good bots and bad bots, and in fact, most bots are used for purposes such as data scraping or scanning the internet for certain things.
You’ve probably used software today that uses bots. A good example is a search engine. The results are usually found after having been indexed by web crawlers, a type of bot that logs details about websites.
Like other digital infections on this list, bad bots (or malware bots) are often embedded in the code of software applications. Popular hosts for malware bots include apps, browser extensions, and software programs.
Once there is a whole bunch of these bots installed, they can then all link together via a command and control centre (C&C).
From here, the controller can link these bots together into a botnet (network of bots) to perform more complex tasks. These can include:
- Denial of service attacks (DDoS)
- Ad fraud (where bots are used to view or click on ads on spoofed websites)
- Stealing data such as keystrokes or files on a device
- Allow access for the C&C operator (or other parties)
- Access IOT devices (internet of things) to take control or steal their data
Here at CHEQ, we’re focused on protecting pay-per-click ads from bot activity or click fraud. These clicks often come from click farms, or from organized botnets looking to reduce your marketing spend.
In terms of click fraud, bad bots are usually programmed to perform an action, such as clicking repeatedly on a specific link or button. Consider that each of those clicks is your money, and you see why they’re bad bots.
Read more about bot traffic and the world of ad fraud bots.
How to avoid or protect against bots
Like all of the malware infections on this list, protecting against bots on your computer or portable device involves caution. A regular scan with a virus scanner and being cautious with downloading or running software.
For marketers running pay-per-click ads, protecting against bots and botnets is a daily challenge. From our own data, we see that bots click around 90% of all ads online every day.
So, if you’re using a PPC ad platform, you’re probably losing at the very least 10% of your ad spend to bots.
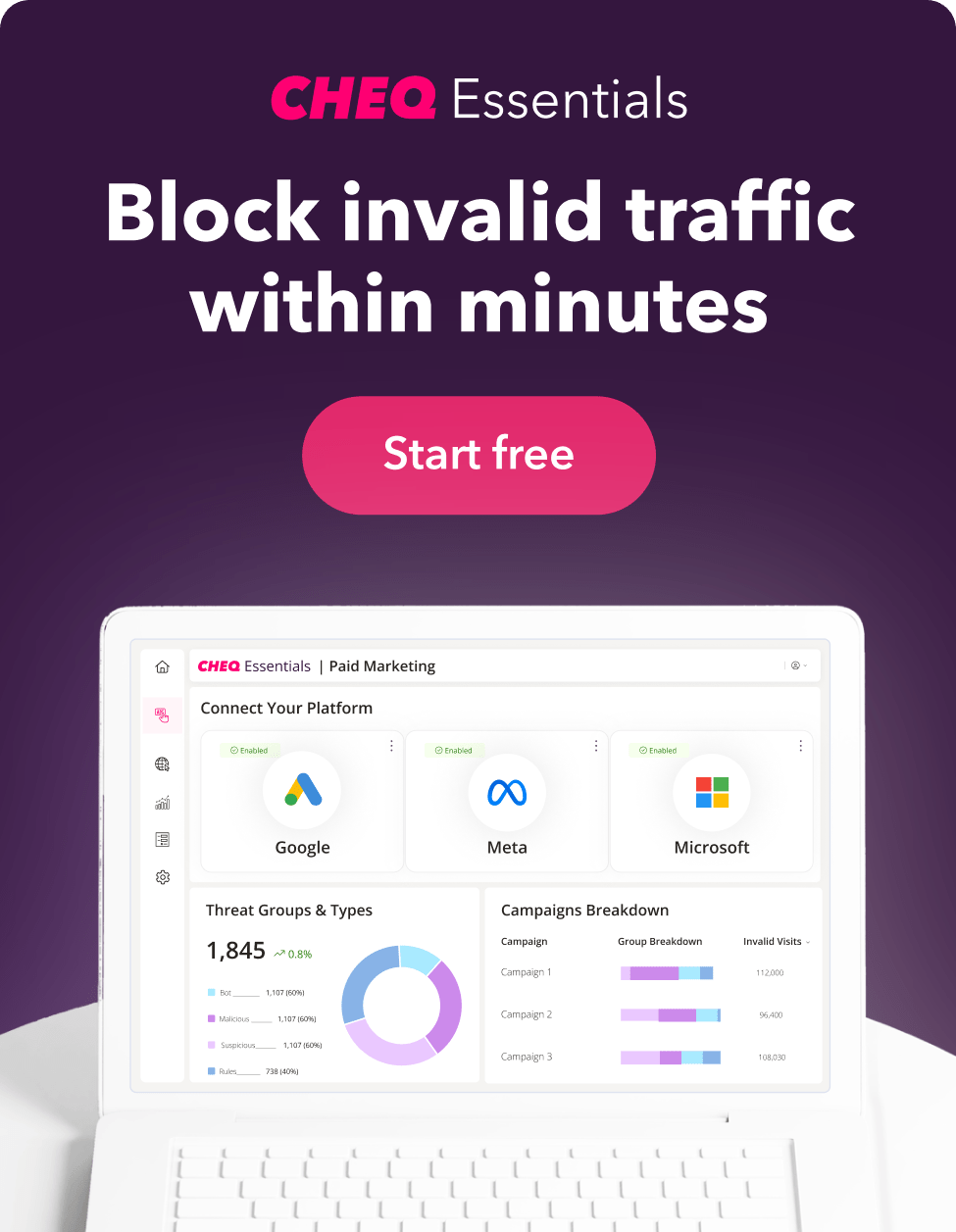
With CHEQ Essentials, we log the identity of each device that clicks on your paid links and make sure that we block those bad bots. If you’re running PPC ads on Google Adwords, Facebook Ads, or Bing Ads, run a diagnostic on your account with our free trial to see how much bot traffic your ads are seeing.
You can find out more about how click fraud works in our guide.
Final thoughts
These digital threats exist because there is a lot of money to be made from cybercrime and online fraud. From ransomware to data theft or click fraud, for hackers, coders, and developers, it’s an easy target.
One of the easiest ways to monetize a network of viruses and bots is to perform advertising click fraud or ad fraud. By making a network of devices infected with malicious code available to others, the operators can monetize their infrastructure.
Blocking bad traffic on your paid ad campaigns will reduce your exposure to this common cybercrime.
Additionally, bad bots can perform all kinds of malicious activity on your site, including finding security vulnerabilities and backdoors. Bot prevention is more important than ever for anyone running a business online.
With CHEQ Essentials, you can prevent invalid traffic (IVT) on your Google Ads, Facebook Ads, and Bing/Microsoft Ads. And now you can also block direct bot traffic on your WordPress site, including carding bots and brute force logins, with bot mitigation.
Although it might feel like it’s a never-ending task defending your data from viruses, bots, and trojans, using software and taking precautions is the best way to avoid becoming a victim.
- Be careful what you download
- Run a regular anti-virus scan
- Use anti-click fraud software and bot traffic protection
Sign up for your free 7-day trial of CHEQ Essentials and get a real look at your ad traffic.