Probably the most infamous click fraud campaigns of all time, Methbot and 3ve have earned their places in notoriety. These two audacious malware campaigns set the scene for much of the current trends in ad fraud and click fraud that we see today. Understanding how they work and their downfall is both a fascinating look at the criminal networks that operate ad fraud and what Pay Per Click (PPC) marketers are up against.
| Name: | Methbot and 3ve (Eve) |
| Status: | Deactivated |
| Summary: | Two of the biggest ad fraud botnets that were used to generate fake impressions on video ads, earning their organisers over $36 million between 2014-2018. |
First spotted by White Ops in 2015, Methbot was originally a fairly low-impact bot signature then known as C3. However, in late 2016, the bot mutated and began to aggressively target ad inventory with an estimated 137 million video impressions per day.
How did Methbot work?
Methbot’s modus operandi was to view video ads on spoofed websites, creating impressions that looked like genuine human activity. The operators of Methbot had obviously put a lot of time, money, and effort into developing the scheme, as it was deceptively simple but devastatingly effective.
Although the Methbot program used infected computers to generate the views, much of the activity was controlled from centralised servers in the USA and Netherlands. These servers ran dedicated proxies which masked the true location of the infected devices, adding in the details of real IP addresses that they had acquired.
At its peak, it’s thought that Methbot was making up to 400,000 impressions per day across its whole infrastructure.
These impressions were all channelled through an incredible 250,000 fake domains, copied (spoofed) from genuine and well-respected websites. Sites on this inventory include some of the best-known and widely visited websites, including:
- The Wall Street Journal
- The Mail Online
- Accuweather
- ESPN
- AOL
- BBC.com
- Business Insider
- CNN
In short, if you can think of a well-known website, it was probably spoofed by the Methbot team. This basically means that the content and identity of these websites were copied onto a lookalike URL which would seem like the real deal.
For advertisers, it would have looked like their video ads were appearing on these high-profile websites and they were getting lots of impressions. Of course, they would have been paying out for those impressions but seeing no corresponding increase in clicks or conversions on their campaigns.

Methbot exposed
When the huge scale was exposed by White Ops, they reported their findings to the FBI, which marked the beginning of the end for Methbot. But, it wasn’t yet the end of this huge and complex ad fraud operation.
At the same time as Methbot was being wound down, a smaller botnet seemed to be scaling up it’s activity. In fact, 3ve (pronounced Eve) had been viewed as a fairly unremarkable bot conducting some low level ad fraud on residential computers.
However in 2017, 3ve began to process more and more ad requests, with estimates of between 3 and 12 billion views a day.
The rise of 3ve
It has now been revealed that several of the same operatives who designed and ran Methbot were also behind 3ve. As the scheme grew, it soon became apparent that Methbot was just the dress rehearsal for this even more elaborate ad bot operation.
And indeed, 3ve was hugely complex, with layers of sub operation, and the use of other Trojans, bots and malware to proliferate the code across more devices. With the ability to work 24/7, the 3ve botnet could collect the payout on even more video ads than even Methbot, which had until now been the biggest botnet operation uncovered.
Although the two botnet operations share many similarities, 3ve was much more advanced and sets the blueprint for a lot of today’s click fraud practices. The key feature that was different from Methbot is that 3ve was mostly based on these remote infected PCs. They both used compromised IP addresses to mask their activity and routed traffic through a huge inventory of spoofed sites.
How did 3ve work?
3ve was based on a complex system of three separate but intertwined botnet systems, all of which did roughly the same thing. As with Methbot, the fraud operators had access to huge amounts of infected devices which they could control remotely to open browsers to visit their spoofed sites and then channel those bots through them.
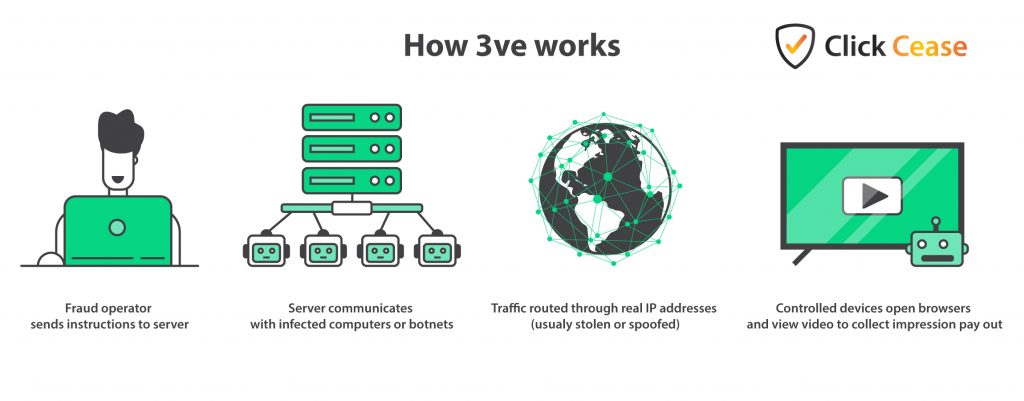
The practice of clicking on ads from a user’s device without their knowledge is, today, pretty old news. But at the time this was cutting-edge stuff and incredibly tricky to check or block.
In fact, 3ve leveraged other botnets in operation at the time, including Kovter and Boaxxe (aka Miuref). These could be used to source those valuable IP addresses used to mask their activity or to channel those high-volume bots.
Although the revenue streams for 3ve were focused mainly on the ad fraud operations, which certainly bought in the highest volumes of income, they had other options too. With their talents, the 3ve botnet operators diversified to offering bot traffic for hire and also selling advertising space on their own spoofed sites. Why not maximise that income, hey?
Who created 3ve and Methbot?
Both of these sophisticated networks were created and operated by a team of criminals, most of whom were from Russia and Kazakhstan. Aleksandr Zhukov, Yevgeny Timchenko, Sergey Denisoff and Sergey Ovsyannikov have all been arrested and charged with conspiracy to commit wire fraud, money laundering, aggravated identity theft and conspiracy to commit computer intrusion.
However, there are at least five other members of this criminal network who are still at large. The practices and processes used by these criminal coders serves as an inspiration for many of today’s click fraud practitioners, and highlights the money that can be made from successful click fraud.
Protecting against click fraud
Today the scale and sophistication of Methbot and 3ve is still very impressive and, to date, they might still be the most profitable ad fraud networks ever. Such bot attacks are part of an ad fraud problem costing marketers $23 billion each year. What these operations reveal is that there is a lot of money to be made for anyone enterprising enough to develop the next big botnet.
Of course, the ad networks such as Google and Facebook are well aware of the practice and put processes in place to protect against fraud. However, as we have seen on this very blog, these processes are often quickly worked around by these enterprising criminals.
Many of the manual processes to protect yourself against PPC fraud can have some effect. But, using ClickCease is one of the most surefire ways of blocking click fraud, no matter what new processes are developed by criminals. With device tracking and IP address blacklisting, ClickCease helps advertisers to keep pace, and even stay one step ahead of click fraudsters.
Whatever threat is out there, make sure you don’t fall victim. Check out ClickCease with a free trial to see how much of a difference it can make to your PPC ad campaigns.
Find out more about click fraud and ad fraud in our in-depth guide.
Sources used in this article:
