A key feature of fraudulent online traffic is that it is often routed through either a Virtual Private Network (VPN) or a proxy server. That’s not to say all traffic from VPNs or proxies is click fraud. But most click fraud can be traced through these gateways.
For the uninitiated, click fraud is the practice of non-genuine traffic clicking on your Google Ads and other PPC campaigns. This non-genuine traffic is also referred to as invalid traffic (IVT), which includes bots, click farms, and even your business competitors clicking on ads to waste your ad spend.
One of the main techniques used to fool the ad platforms is the use of VPNs and proxy servers to hide the fraudulent IP address, allowing the fraud to continue.
VPN click fraud is a common problem that we see here at ClickCease. So, we want to share how VPN and proxy servers can be used to hide traffic and how it works.
Proxy Servers
They hide your IP, but you are still not invisible…
“A proxy server is a computer that offers a computer network service to allow clients to make indirect network connections to other network services. A client connects to the proxy server, then requests a connection, file, or other resource available on a different server. The proxy provides the resource either by connecting to the specified server or by serving it from a cache. In some cases, the proxy may alter the client’s request or the server’s response for various purposes.”
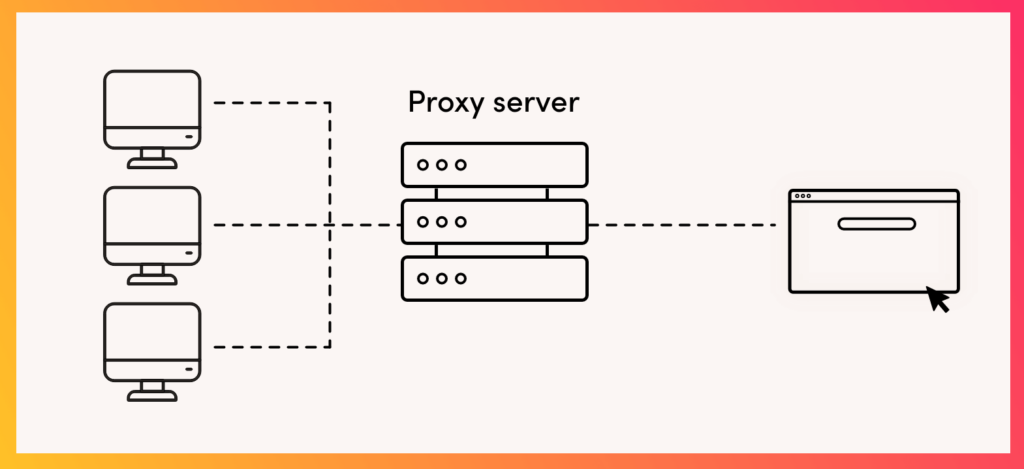
How does a proxy server work?
Simply put, a proxy server is a computer used as a form of middle-man. By routing your traffic through a proxy server, you are masking your internet activities in a way that they appear to be originating from somewhere else.
However, in most cases, proxy servers do not strip your internet transmissions of identifiable information- meaning there are no additional privacy or security considerations built into it.
Furthermore, proxies are configured on an application-by-application basis and not computer-wide. This means only one application at a time (your web browser or your BitTorrent client, for example) can be configured for use with a proxy server.
This configuration is great when you want to perform a low-stake task, such as reaching simple region-restricted content (Youtube/Netflix, anyone?) or bypassing IP-based restrictions on services.
It’s also a popular method for click fraud operators to hide their location with fake proxy, as the fraudulent device mostly only uses one application. We’ll dive into the details of how fraudsters execute their attacks with the help of proxies a bit later in the article.
Private and shared proxy servers
As well as these three tiers of proxy servers, proxy users can also choose either a private or shared proxy service. Some are totally free, for example, the TOR browser, which uses a network of computers around the world to enable users to remain anonymous. However, professional proxy users, especially those performing ad fraud or click fraud, will most likely use a dedicated private proxy.
These private proxy servers are often based in data centers like AWS (Amazon Web Services).
And setting up a private proxy server to use for your click fraud campaign is actually very easy.
Virtual Private Networks (VPNs)
Your connection is encrypted, and you become much harder to track and identify…
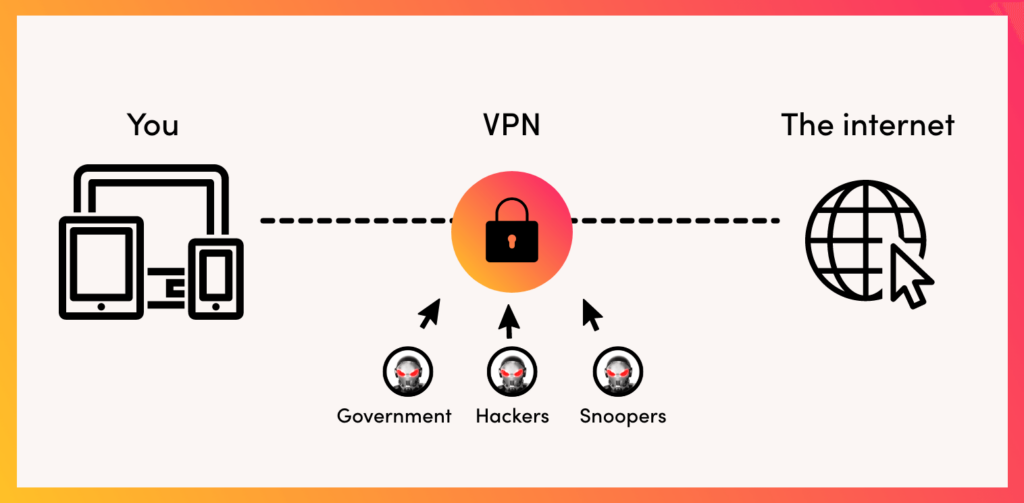
Virtual Private Networks (VPNs) are secure online tunnels that protect your internet connection by encrypting data between your device and the server. This hides your online activity from third parties and increases your privacy.
Businesses often use VPNs to protect their employees’ data when they are working remotely. They can also be used by individuals to protect their privacy and security when they are using public Wi-Fi networks.
Your connection is encrypted, and you become much harder to track and identify… And this, unfortunately, is where fraudsters have identified an advantage to hide their activities.
How do VPNs work?
VPNs, in a similar fashion to proxies, make your internet activity appear as if it is originating from a far away location. But that’s where the similarities pretty much end.
First off, unlike proxies, VPNs are configured to be set up at the device level. Moreover, the VPN connection uses the full network connection of the device it is configured on. Also, the connection between the user’s device and the VPN server is done via a heavily encrypted tunnel. That is why VPNs are considered superior when it comes to performing high-stakes tasks where privacy or higher security is a concern. In fact, studies indicate that 13.6% of all fraudulent traffic is attributed to VPN click fraud, highlighting the significant role they play for fraudsters.
So, what makes VPNs and proxies attractive methods to fraudsters?
Nowadays, whenever an IP address is blocked in the Google Adwords or Bing Ads platforms, the advertiser’s ads become invisible to the attacker. This results in the attacker being unable to click on the advertiser’s ads any longer.
However, by employing a proxy server or by using a VPN, the attacker can rapidly change IP addresses regularly and click on the advertiser’s ads again and again. This is VPN click fraud.
Organized ad fraud or click fraud operators will use a high-level proxy server or VPN to hide their identity and perform their fraud. And because these fraudulent operations are often organized and use multiple devices, switching IP addresses is instrumental in performing this level and volume of fraud.
Other forms of click fraud, including traffic bots for hire, also use VPNs and proxies to hide their location and device.
How do VPNs and proxies are used for click fraud?
As we’ve seen, VPNs and proxies are appealing tools for fraudsters due to their ability to mask their malicious online activities effectively. The dynamic nature of these services minimizes the risks of identification for fraudsters.
To understand them better, here’s a breakdown of how fraudsters employ VPNs and proxies in some of their common click fraud methods:
IP spoofing
VPN: With VPN services, fraudsters can easily hide their actual IP addresses, making it appear as if clicks are coming from various locations. This helps them avoid detection based on IP patterns.
Proxy: Similar to VPNs, proxy servers can be used to spoof IP addresses. By rotating through different proxies, fraudsters make it difficult for advertisers to identify and block fraudulent traffic.
Geotargeting manipulation
VPN: Fraudsters can use VPN servers located in specific geographic regions to simulate legitimate traffic from targeted locations. For example, a fraudster could use a VPN to make it appear as if they are located in the United States in order to click on ads that are only targeted to US users.
Proxy: Proxies work in a very similar way to VPNs when it comes to masking geotargeting locations. It’s just that the internet traffic is routed through the proxy server, while in the case of VPN, the traffic is fully encrypted through a secure tunnel which makes it more difficult to be identified.
Rotating IPs
VPN: Fraudsters may utilize VPN services with features like automatic IP rotation. This constantly changes the IP address associated with clicks, making it challenging for ad networks and businesses to identify suspicious patterns.
Proxy: Similar to VPNs, proxy servers can be set up to rotate IP addresses, making it more difficult for advertisers to trace fraudulent activity back to a single source.
Automated scripts and bots
VPN: Automated browsing scripts and bots can be deployed in conjunction with VPN services to simulate human-like interactions. A VPN bot helps fraudsters generate clicks and engage with ads in a way that mimics legitimate user behavior.
Proxy: Bots and scripts can also be used with proxy servers to automate fraudulent activities such as clicking on ads. The combination of fake proxies and automation makes it challenging for detection systems to differentiate between real and fake traffic.
User-agent spoofing
VPN: Fraudsters may modify the user-agent strings of their browsers while using VPNs to mimic different devices and browsers. This makes identifying and blocking fraudulent activity harder based on user-agent patterns.
Proxy: Similar to VPNs, user-agent spoofing with proxy servers involves altering browser information to appear as if clicks come from diverse devices and browsers, making it more difficult for advertisers to detect automated or suspicious behavior.
Click farms
VPN: Click farms may use VPN services to generate clicks from various locations, contributing to the fake appearance of diverse and legitimate traffic sources.
Proxy: Similarly, click farms can leverage proxy servers to simulate clicks from different IP addresses, further complicating efforts to identify and block fraudulent activity.
How does ClickCease combat proxy and VPN click fraud?
Anonymity poses a considerable challenge when it comes to combating this type of fraud. The issue for the major ad platforms is that they will mostly focus on blocking IP addresses as a way to stop click fraud. This has been shown to be largely ineffective because, as we’ve seen, IP addresses can easily be switched by click farms or botnet operators.
However, here at ClickCease, we have developed several solutions for blocking proxy servers and VPNs.
We have accumulated and compiled a large amount of data regarding known repeating offenders into blacklists which we use as the first tier of protection against fraudsters who use proxy servers and VPNs.
Secondly, alongside these blacklists, we allow our clients to determine their click threshold, which refers to the maximum amount of clicks they would allow any one IP address to be able to click on their ads before our system automatically blocks them.
Thirdly, we have devised a tool that allows our system to tag each individual device used by any IP address with a specific and unique ID. This means that even though the fraudster who’s assaulting your ads might be trying to hide his IP address by constantly changing it, we are still able to identify that it is indeed the same attacker using the same device.
Once we have identified his device as one that is used for fraudulent activity, we are able to block any new IP he uses on its first click.
Find out more about click fraud in our guide.
Is click fraud a problem for you?
If you run PPC ads, there is a very high chance that your campaigns are affected to some extent by VPN click fraud. In fact, 90% of Google Ads campaigns are affected by invalid traffic of some kind.
The average Google Ads campaign actually sees a click fraud rate of around 14%, although, for competitive industries, this can run as high as 70%!
So, is click fraud affecting your Google Ads? Well, the best way to find out is to run a traffic audit to see exactly who or what is clicking your paid ads.
Sign up for your FREE 7-day trial of ClickCease to perform your own traffic audit and to find out if VPN or proxy-based click fraud impacts your campaigns.