There are many sneaky practices employed by digital fraudsters, one of these, clickjacking, has many applications. You might have heard of clickjacking in the past, or perhaps been aware of the potential for this nefarious practice to cause damage online.
So what exactly is clickjacking? And in terms of pay per click ads, how can it be used for click fraud or ad fraud?
Read our complete guide to click fraud and ad fraud here
What is Clickjacking?
Clickjacking is a portmanteau of the words click and hijacking. Put simply, it’s a method used to trick web users to click on an embedded link. The real link is usually either hidden or obscured in some manner, sometimes by an overlay or other technical element that the user isn’t aware of.
The use of clickjacking is often found in malware apps, but can also be found on websites, browser extensions, and other online platforms.
Clickjacking can be used for many purposes including:
- Clicking on a hidden download link (often malicious, e.g; a virus/Trojan download)
- Activating a program such as a cryptocurrency miner or software downloader
- Generating fake engagement with a social media post (such as a ‘Like’)
- Authorising control for a third party to access a device or perform actions remotely (command and control)
- Clicking on hidden ads for click fraud purposes
When the user clicks on the link, the click action is performed on the hidden element. The element is normally embedded in an iFrame with a transparent layer, which hides the link or button beneath.
For example, a box with Click Here might look like it’s the link for the download you’re looking for. But, in fact, it masks the button to a display ad on an external website, or a download or macro designed to gain access to a device.
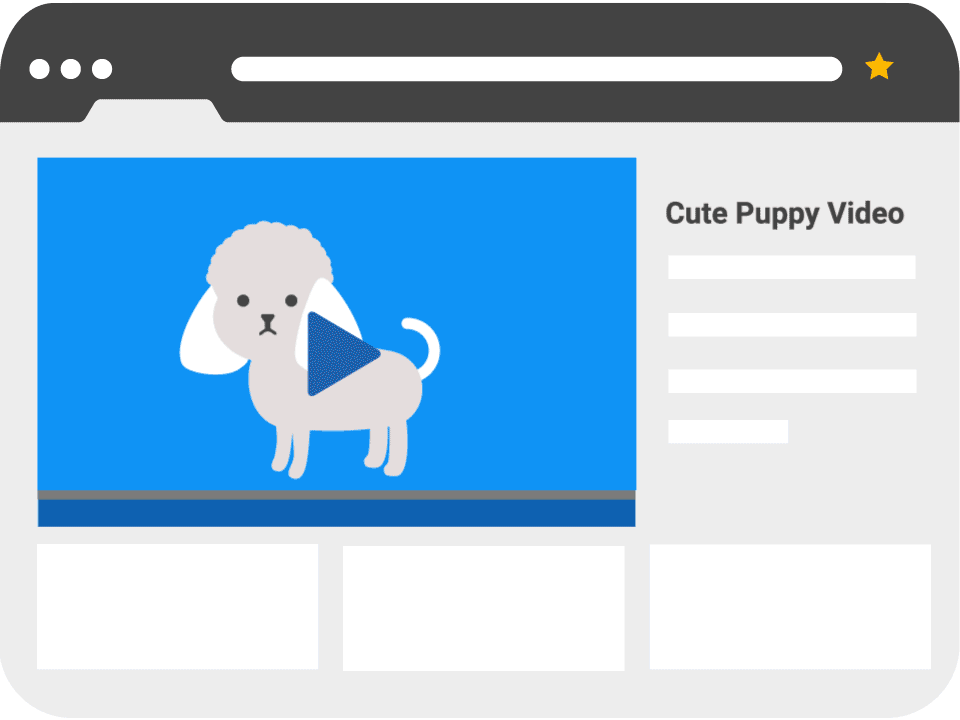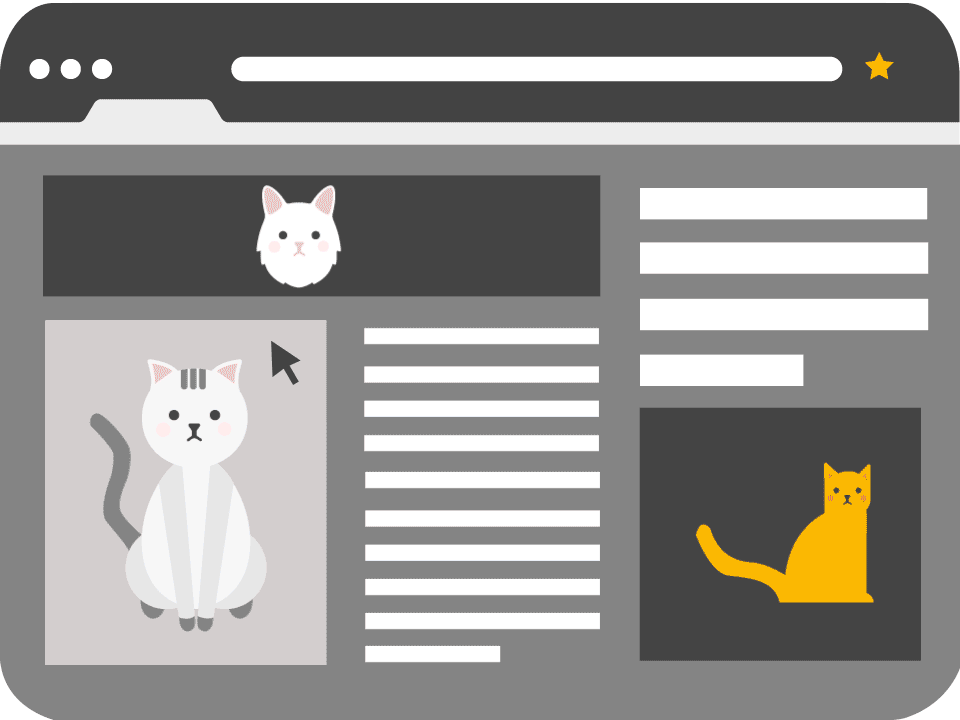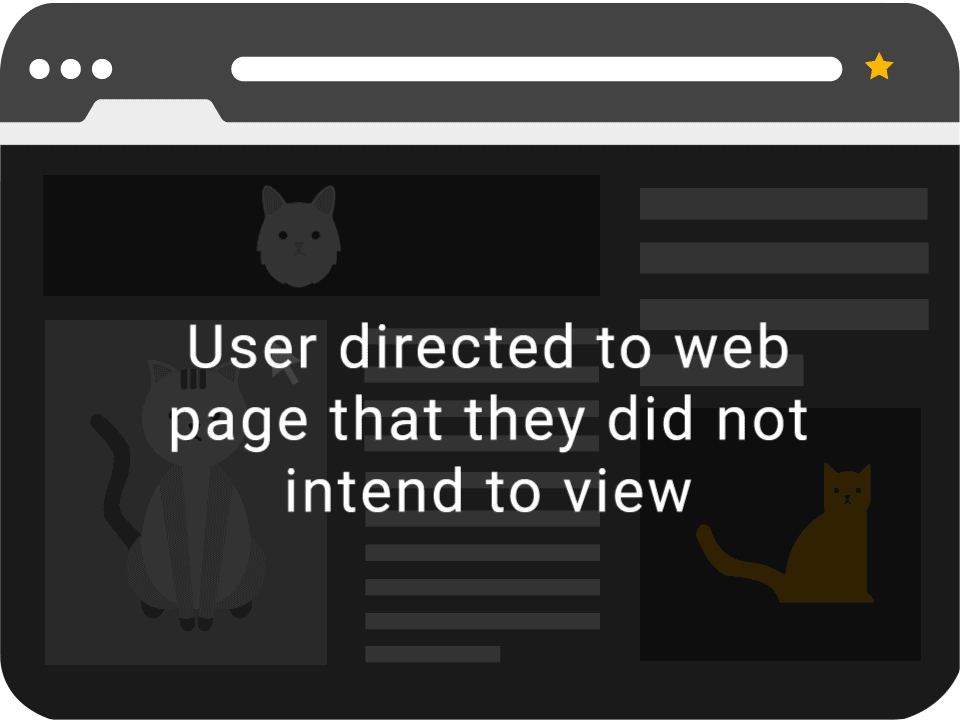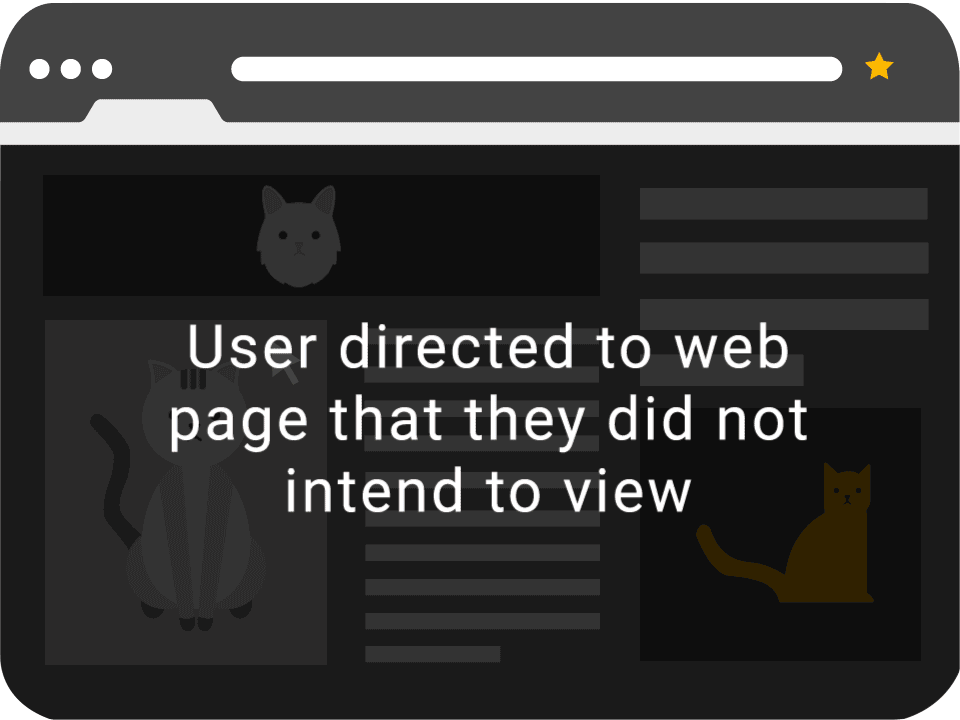
A common method for disguising the layer is using Facebook ‘Like’ buttons, video players or sometimes displaying content with clickbait-style titles.
Also known as click interception, or a UI redress attack, it’s a technique that has been around for many years and has even been used in ad fraud campaigns.
Like all forms of technical fraud, there are several ways a sneaky coder can generate clickjacking on their website or app.
Invisible or Transparent overlay
This method, which was mentioned above, is probably the easiest and most common way to hijack a click.
A site contains an iframe (a HTML frame which can have elements placed inside it) – often with a call to action.
The invisible box laid over the top then collects the click and performs the malicious action (such as clicking an external ad, downloading the software etc).
Hidden Overlay
When visiting a website, a 1×1 pixel (or any size invisible area) is placed under the cursor meaning that any click on the site can be hijacked.
Although this is popular with sites visited by desktop computers, the same techniques are often also applied to apps using click injection style malware. A single click or touch can be diverted to a hidden action for whatever purpose the fraudster wants…
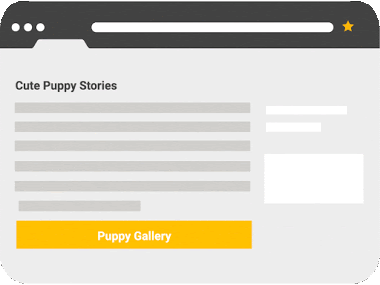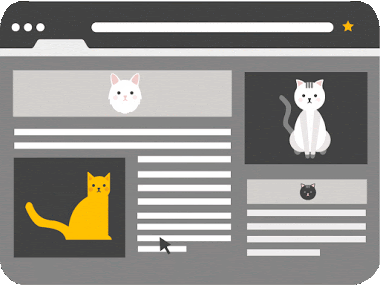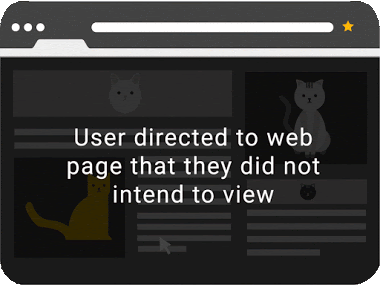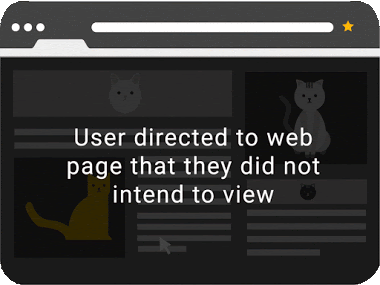
Click Event Dropping
A fraudulent website (for example, one packed full of display ads) is hidden under a genuine website.
But, the fraudulent coder can set all actions on the top layer to register on the lower layer only, generating clicks on the (hidden) site below.
Other Clickjacking Methods
This is just a small selection of the techniques used to hijack clicks for pay per click fraud.
There can also be clever obfuscation methods that encourage users to click in a specific order, or to accept commands via pop up boxes which are often used for malware downloads, stealing data or running other fraudulent actions.
PPC Ads and Click Interception
In terms of modern ad fraud and click fraud, clickjacking is a common problem. And it’s one that continues to be embraced by the criminal coding community.
With the focus on stopping bots and click farms, clickjacking offers fraudsters a clever way to collect genuine clicks and monetise them in a variety of ways.
This can be especially useful for hidden ads on pornographic websites or the niche ‘fake news’ or ‘hate speech’ websites which would normally find it hard to monetise their content.
Clickjacking in click fraud is mostly done via apps or mobile web pages, where it is easy to generate a fake organic click or touch. Often, with one touch, a device can generate a whole host of signals that can be harnessed by the malware elements of an app, referred to as click injection or click spamming.
Although clickjacking does share some similarities with the practice of click injection, the key difference is not using automation to generate clicks.
It’s also worth noting that clickjacking can refer to a number of practices whereby the real purpose of a click or engagement is hidden from the user. This includes ‘cookiejacking’ and ‘cursorjacking’ which are totally different but not completely unrelated techniques.
Spotting and Preventing Clickjacking
There are measures in place to prevent clickjacking on platforms such as Google Ads, such as making it difficult to place websites hosting ads inside iFrames. However, that’s not to say it can’t be done (and it does happen).
Like most fraudulent clicks, the tell tale sign is often factors such as:
- High bounce rate
- Unusual source or location
- IP address indiscrepancies
By default, Google does quite a bit to prevent clickjacking on their ads. For example, they make placing PPC ads in iframes difficult to do, making it less likely that this will be a headache for most. But… It does still happen.
Web masters are encouraged to use X Frame Options to ensure that no part of their website can be embedded on another website.
If you’re running PPC ads and you think you might be seeing clickjacking attacks on your ads, you will most likely see repetitive IP addresses on your dashboard. By using software such as ClickCease, you can easily monitor and block suspicious activity on Google Ads and Bing Ads.
The techniques used to conduct ad fraud and click fraud continue to evolve at lightning pace. Anti-click fraud software such as ClickCease is the best way to stay ahead of those sneaky practices and ensure your PPC ads are seen only by genuine potential customers.
Discover more about click fraud and ad fraud, and how to protect yourself, on our blog